1337UPEasyCTF Challenge
In Plain Sight
In Plain Sight
2024-11-17
##Challenge Name: In Plain Sight
###Solves
- >Solves: 465
- >Points: 50
###Description
Barely hidden tbh..
Attachment: meow.jpg
###Approach
- >
Initial Analysis:
- >Downloaded the attached image (
) and opened it. It appeared to be a normal picture of a cat with no visible clues.meow.jpg
- >Downloaded the attached image (
- >
Checking Metadata:
- >Used
to inspect the image metadata:exiftoolbashexiftool meow.jpg - >No relevant information was found in the metadata.
- >Used
- >
Analyzing the File Contents:
- >Ran the
command to look for hidden text:stringsbashstrings meow.jpg - >Found two interesting pieces of information:
- >A reference to a file named
.flag.png - >A string that resembled a password:
.YoullNeverGetThis719482
- >A reference to a file named
- >Ran the
- >
Identifying Hidden Data:
- >Used
to analyze the file for embedded data:binwalkbashbinwalk meow.jpg - >The analysis revealed an embedded archive.
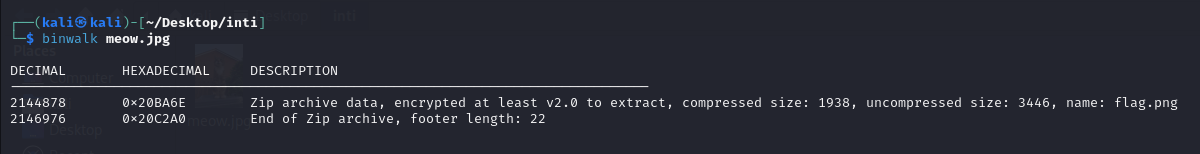
Image1 - >Used
- >
Extracting the Archive:
- >Extracted the hidden archive using
:binwalkbashbinwalk -e meow.jpg - >The archive required a password to unlock. Entered the discovered password
.YoullNeverGetThis719482
- >Extracted the hidden archive using
- >
Inspecting the Extracted File:
- >The extracted archive contained a file named
. Upon opening it, it appeared to be a solid white image.flag.png
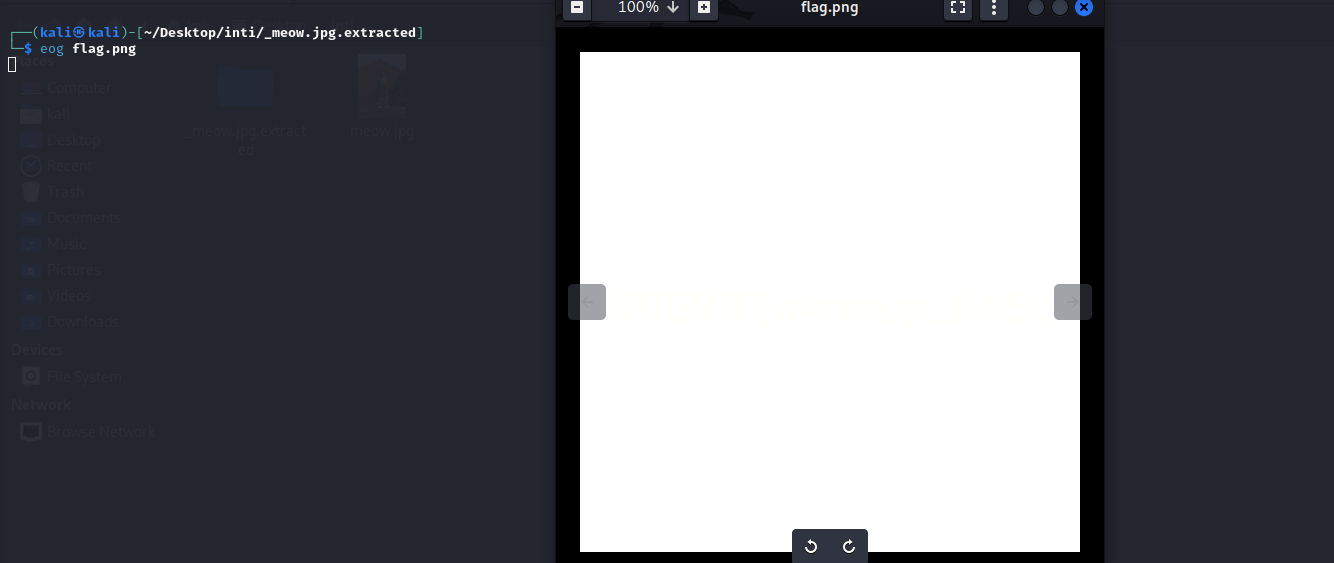
Image2 - >The extracted archive contained a file named
- >
Using Steganography Tools:
- >Opened
in Stegsolve, a tool for analyzing images for hidden data.flag.png - >Switched through the various color map filters and discovered the flag under the Random Color Map 1.
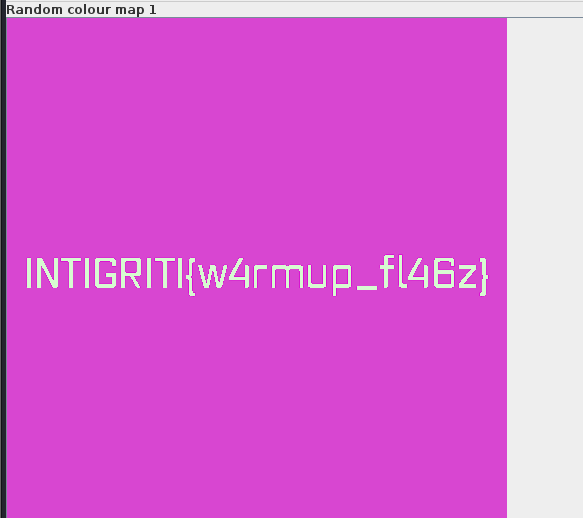
Image3 - >Opened
- >
Flag Found:
INTIGRITI{w4rmup_fl46z}
###Flag
INTIGRITI{w4rmup_fl46z}